
Defining the Future of Cyber Risk Management
We work with consultant groups, system integrators, and nearly 60% of the largest US energy producers to find new ways of protecting critical infrastructure.
Built by Former Risk Managers
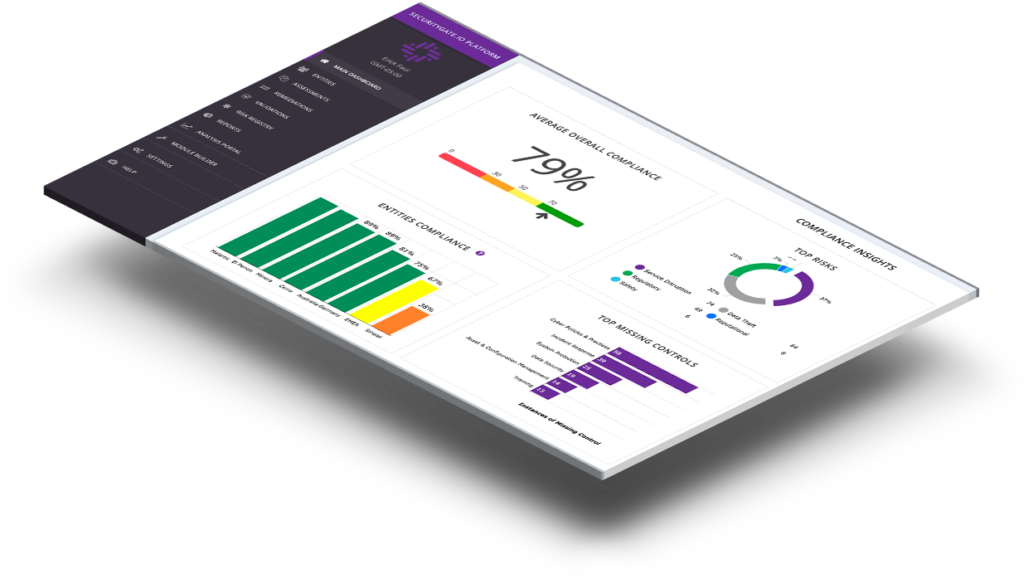
Our team knows critical infrastructure . The SecurityGate.io platform was created to answer the challenges risk managers face in an increasingly digitized world.
We work with leaders in the industry to help organizations reduce the burden of the risk assessment process and close the gap between traditionally siloed teams.
For Critical Infrastructure Organizations at All Levels of Maturity
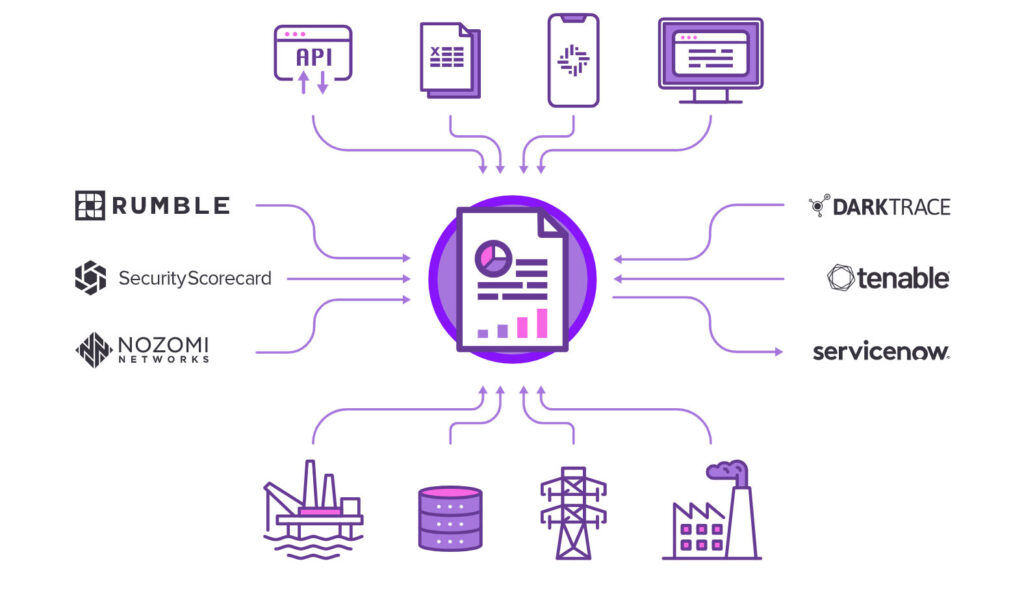
By partnering with other leaders in OT/ICS security, the SecurityGate.io platform provides teams with deeper insights into their environment and enables leaders to confidently make an informed decision with everything at their fingertips.
From small teams to global enterprises, critical infrastructure organizations and consultants of all sizes, types, and maturity levels rely on SecurityGate.io to develop and refine their cyber programs.




SECURITYGATE.IO NAMED IN GARTNER REPORT
2021 Gartner Market Guide for Operational Technology (OT) Security
AVAILABILITY & TECH STACK
SecurityGate.io is deployed across 75 sites around the globe, across all categories of critical infrastructure.
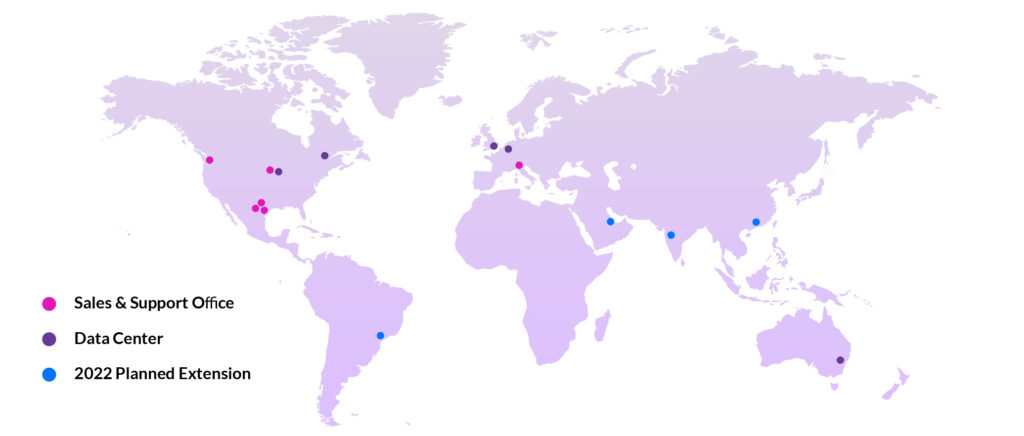
- Secure cloud environment hosted with Amazon Web Services
- 2 Factor Authentication secures user access
- All data is encrypted by default
- Optional ability to bring your own encryption key(s) for further data security

